If you are a customer of KPN and using their internet or IPTV services, you may want to replace their Experia Box. In my case, I wanted to replace this modem with my own Ubiquiti EdgeRouter X. Here are the changes I made to the router’s configuration to get internet and IPTV to work.
Note: VOIP configuration is not included in the below examples.
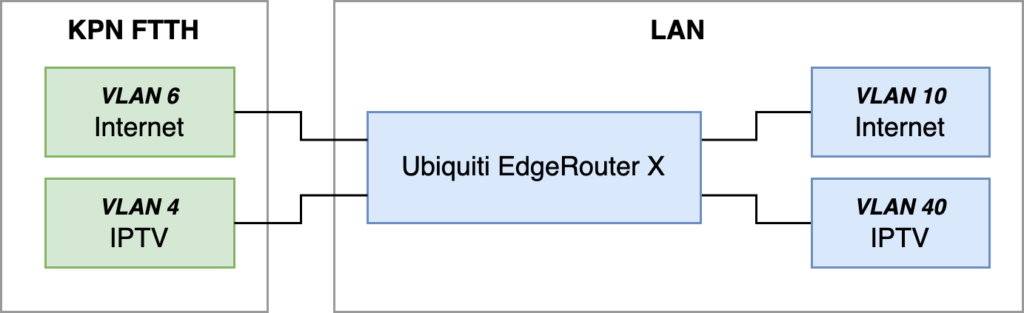
General setup
We will use the following setup as a reference:
Our first goal is to get IPv4 and IPv6 internet working through the EdgeRouter for our internal VLAN 10. If that works, we are going to implement IPTV networking for internal VLAN 40. I will describe the configuration required to set this up, but will leave out a lot of default values and settings that are irrelevant in getting this to work.
KPN has provided their own documentation for using your own modem. Make sure to read through that page so you understand what you are configuring.
Setting up KPN IPv4 internet
We start off by documenting the physical interface that our EdgeRouter is using to connect with the KPN FTTH device, in my case eth3:
interfaces {
ethernet eth3 {
description "KPN uplink"
}
}
Next, enable VLANs on your switch0 and set up the VLANs 4 and 6 that are present on KPN’s side:
interfaces {
switch switch 0 {
switch-port {
interface eth3 {
vlan {
vid 4
vid 6
}
}
vlan-aware enable
}
}
}
Let’s get KPN internet working over IPv4. It is required to set up a PPPoE connection with them, in which our internet traffic will be encapsulated. We set this connection up in the vif 6 of the switch:
interfaces {
switch switch0 {
mtu 1512
vif 6 {
description "KPN Internet"
mtu 1508
pppoe 0 {
default-route auto
description "KPN Internet PPPoE"
idle-timeout 180
mtu 1500
name-server auto
password internet
user-id internet
}
}
}
}
service {
nat {
rule 5000 {
description "Masquerade for WAN"
outbound-interface pppoe0
type masquerade
}
}
}
Some notes on the above snippet:
- Packets inside the
pppoe 0tunnel are required to have an MTU of 1500. The outside MTUs of 1508 and 1512 allow for the increased size of the packets as a result of the packet headers. - It should not matter what you use for
user-idorpassword. - The NAT rule will make sure that all outgoing packets will use your KPN WAN IPv4 address as the source IP address.
The KPN IPv4 side of things should now be working – it’s time to configure our internet VLAN 10!
interfaces {
switch switch0 {
switch-port {
interface eth0 {
vlan {
vid 10
}
}
}
vif 10 {
address 10.10.0.1/16
description Private
}
}
}
service {
dhcp-server {
disabled false
shared-network-name vlan10-private {
authoritative enable
subnet 10.10.0.0/16 {
lease 86400
start 10.10.1.1 {
stop 10.10.1.254
}
}
}
use-dnsmasq enable
}
dns {
forwarding {
cache-size 10000
listen-on switch0.10
name-server 8.8.8.8
name-server 1.1.1.1
options strict-order
}
}
}
This should be enough to get IPv4 internet working on your VLAN 10!
- I use the subnet
10.10.0.0/16for VLAN 10. Make sure you update both the virtual interface and the DHCP server if you want to use a different subnet. - I have found
dnsmasqto work better as a DHCP server than the built-indhcpd, but your mileage may vary. Removeuse-dnsmasq enableif you’d like to trydhcpdinstead. - I’ve provided two DNS servers (Google and CloudFlare) as an example.
After verifying that internet works, let’s make sure to set up our IPv4 firewall:
firewall {
ip-src-route disable
log-martians enable
name ipv4-private-out {
default-action drop
description "IPv4 traffic to private VLAN"
rule 10 {
action accept
description "Allow related traffic"
state {
established enable
related enable
}
}
}
name ipv4-wan-in {
default-action drop
description "IPv4 traffic from WAN to internal network"
rule 10 {
action accept
description "Allow established/related"
state {
established enable
related enable
}
}
rule 20 {
action reject-tcp
description "Reject invalid conntrack with TCP reset"
protocol tcp
state {
invalid enable
}
}
rule 30 {
action reject
description "Reject invalid conntrack"
state {
invalid enable
}
}
}
name ipv4-wan-local {
default-action drop
description "IPv4 traffic from WAN to local router"
rule 10 {
action accept
description "Allow established/related"
state {
established enable
related enable
}
}
rule 20 {
action accept
description "Allow ping"
protocol icmp
}
}
name ipv4-wan-out {
default-action drop
description "IPv4 traffic from internal network to WAN"
rule 10 {
action accept
description "Allow new and related traffic"
state {
established enable
new enable
related enable
}
}
rule 20 {
action reject-tcp
description "Reject invalid conntrack with TCP reset"
protocol tcp
state {
invalid enable
}
}
rule 30 {
action reject
description "Reject invalid conntrack"
state {
invalid enable
}
}
}
receive-redirects disable
send-redirects enable
source-validation disable
syn-cookies enable
}
interfaces {
switch switch0 {
vif 6 {
pppoe 0 {
firewall {
in {
name ipv4-wan-in
}
local {
name ipv4-wan-local
}
out {
name ipv4-wan-out
}
}
}
}
vif 10 {
firewall {
out {
name ipv4-private-out
}
}
}
}
}
Setting up KPN IPv6 internet
The basic configuration for KPN IPv6 is relatively easy. However, the EdgeRouter X device requires a fix to one of its scripts in order to get an IPv6 address, which is discussed later on.
Start off with enabling IPv6 on the pppoe0 interface and VLAN 10:
interfaces {
switch switch0 {
vif 6 {
pppoe 0 {
dhcpv6-pd {
pd 0 {
interface switch0.10 {
no-dns
prefix-id :1
service slaac
}
prefix-length /48
}
rapid-commit enable
}
ipv6 {
address {
autoconf
}
dup-addr-detect-transmits 1
enable {
}
}
}
}
vif 10 {
ipv6 {
address {
autoconf
}
dup-addr-detect-transmits 1
}
}
}
}
Next, we need to add a static route to send all outgoing IPv6 packets over the pppoe0 interface:
protocols {
static {
interface-route6 ::/0 {
next-hop-interface pppoe0 {
}
}
}
}
Finally, we need to apply a patch on the EdgeRouter X device to fix a bug – this is still relevant as of release 2.0.9-hotfix.7:
--- a/opt/vyatta/share/perl5/Vyatta/Interface.pm
+++ b/opt/vyatta/share/perl5/Vyatta/Interface.pm
@@ -212,14 +212,14 @@ sub ppp_path {
$path = "interfaces ethernet $intf pppoe $id";
} elsif ($intf =~ /(peth\d+)/) {
$path = "interfaces pseudo-ethernet $intf pppoe $id";
- } elsif ($intf =~ /(switch\d+)/) {
- $path = "interfaces switch $intf pppoe $id";
} elsif ($intf =~ /(switch\d+)\.(\d+)/) {
$path = "interfaces switch $1 vif $2 pppoe $id";
- } elsif ($intf =~ /(bridge\d+)/) {
- $path = "interfaces bridge $intf pppoe $id";
+ } elsif ($intf =~ /(switch\d+)/) {
+ $path = "interfaces switch $intf pppoe $id";
} elsif ($intf =~ /(bridge\d+)\.(\d+)/) {
$path = "interfaces bridge $1 vif $2 pppoe $id";
+ } elsif ($intf =~ /(bridge\d+)/) {
+ $path = "interfaces bridge $intf pppoe $id";
}
return $path if defined $path;
}
For more instructions and context, see the source post for this patch. After rebooting your EdgeRouter, IPv6 internet should be working!
As with IPv4, let’s introduce the firewall next:
firewall {
ipv6-name ipv6-wan-in {
default-action drop
description "IPv6 traffic from WAN to internal network"
rule 10 {
action accept
description "Allow related traffic"
state {
established enable
related enable
}
}
rule 20 {
action accept
description "Allow ICMPv6"
protocol icmpv6
}
}
ipv6-name ipv6-wan-local {
default-action drop
description "IPv6 traffic from WAN to local router"
enable-default-log
rule 10 {
action accept
description "Allow established/related"
state {
established enable
related enable
}
}
rule 20 {
action accept
description "Allow DHCPv6"
destination {
port 546
}
protocol udp
source {
port 547
}
}
rule 30 {
action accept
description "Allow ICMPv6"
protocol ipv6-icmp
}
}
ipv6-receive-redirects disable
ipv6-src-route disable
}
interfaces {
switch switch0 {
vif 6 {
pppoe 0 {
firewall {
in {
ipv6-name ipv6-wan-in
}
local {
ipv6-name ipv6-wan-local
}
}
}
}
}
}
It is important to allow ICMPv6 traffic from the WAN. While ICMP is largely irrelevant for IPv4, the protocol plays a major role in proper handling of IPv6 connections.
Setting up KPN IPTV
Let’s configure KPN’s VLAN 4 first:
interfaces {
switch switch0 {
vif 4 {
address dhcp
description "KPN IPTV"
dhcp-options {
client-option "send vendor-class-identifier "IPTV_RG";"
client-option "request subnet-mask, routers, broadcast-address, rfc3442-classless-static-routes;"
default-route no-update
default-route-distance 210
name-server update
}
mtu 1500
}
}
}
service {
nat {
rule 5001 {
description IPTV
outbound-interface switch0.4
protocol all
type masquerade
}
}
}
We need to send those very specific DHCP options to KPN’s DHCP server – without those options, we may not get an IP address assigned.
Now we have KPN’s VLAN 4 network up and running, let’s configure our VLAN 40 for internal IPTV traffic with two TV boxes connected directly at eth1 and eth2:
interfaces {
switch switch0 {
switch-port {
interface eth1 {
vlan {
pvid 40
}
}
interface eth2 {
vlan {
pvid 40
}
}
}
vif 40 {
address 10.40.0.1/16
description IPTV
}
}
}
service {
dhcp-server {
shared-network-name vlan40-iptv {
authoritative enable
subnet 10.40.0.0/16 {
lease 86400
start 10.40.1.1 {
stop 10.40.1.254
}
}
}
}
dns {
forwarding {
listen-on switch0.40
}
}
}
Again, if you are using something different than 10.40.0.0/16 for your internal VLAN, make sure to update those values. If you have connected a VLAN-aware switch to a physical port of your EdgeRouter, use vid instead of pvid.
We have now set up the IPTV networks, DHCP and DNS – but in order for IPTV to start working, we will need to support the IGMP protocol. KPN’s Experia Box has a built-in IGMP proxy that takes care of IGMP group management, so we will need an IGMP proxy as well:
protocols {
igmp-proxy {
interface pppoe0 {
role disabled
threshold 1
}
interface switch0.4 {
alt-subnet 0.0.0.0/0
role upstream
threshold 1
}
interface switch0.10 {
role disabled
threshold 1
}
interface switch0.40 {
alt-subnet 10.40.0.0/16
role downstream
threshold 1
}
}
}
We configure igmp-proxy to use KPN VLAN 4 (switch0.4) as upstream and internal VLAN 40 (switch0.40) as downstream. After saving and committing this configuration, our TV boxes should be working!
The only thing left to do now, is to configure the IPTV firewall:
firewall {
name ipv4-iptv-local {
default-action drop
description "IPv4 traffic from IPTV VLAN to local router"
rule 10 {
action accept
description "Allow ICMP to local router"
protocol icmp
}
rule 20 {
action accept
description "Allow DHCP"
destination {
port 67
}
protocol udp
}
rule 30 {
action accept
description "Allow DNS"
destination {
port 53
}
protocol udp
}
rule 40 {
action accept
description "Allow IGMP"
protocol igmp
}
}
name ipv4-kpn-iptv-in {
default-action drop
description "IPv4 IPTV traffic from KPN to internal network"
rule 10 {
action accept
description "Allow related traffic"
state {
established enable
related enable
}
}
rule 20 {
action accept
description "Allow IPTV broadcasts"
destination {
address 224.0.0.0/4
}
protocol udp
}
}
name ipv4-kpn-iptv-local {
default-action drop
description "IPv4 IPTV traffic from KPN to local router"
rule 10 {
action accept
description "Allow IGMP"
protocol igmp
}
}
name ipv4-kpn-iptv-out {
default-action drop
description "IPTV traffic from internal network to KPN"
rule 10 {
action accept
description "Allow traffic from IPTV subnet"
source {
address 10.40.0.0/16
}
}
}
}
interfaces {
switch switch0 {
vif 4 {
firewall {
in {
name ipv4-kpn-iptv-in
}
local {
name ipv4-kpn-iptv-local
}
out {
name ipv4-kpn-iptv-out
}
}
}
vif 40 {
firewall {
local {
name ipv4-iptv-local
}
}
}
}
}
Let me know if this has helped you set up your internet and IPTV!